Wireless networks have become ubiquitous. We use them at home, work, mall, airport, coffee shop and just about everywhere else we go. When setting up a wireless network, it’s wise to spend some quality time considering how you plan to use that network. One important question to consider, is will guests be allowed to have network access. If your answer is yes, the next question to consider is how are you going to protect yourself. It’s not very wise to allow unfettered guest access to your production network where one can poke around and, with a little bit of ingenuity, gain access to data and resources that they shouldn’t have access to.
I recently set up a new office and as part of that process wanted to make provision for guest internet access, but I didn’t want to set up separate access points for employees and guests. I knew Apple had functionality to allow for the creation of guest networks via their Airport products but was a bit skeptical that it would work for me because Apple assumes you are using an Airport Extreme as your primary router. I would never use such a device as my primary router but, as always, where there’s a will, there is a way. Airport Expresses are cheap so I figured I would buy one and give it a shot.
Windows Airport Utility Issue
After receiving my Airport Express (I really bought three) I set it up and then downloaded the latest Airport Utility for Windows (5.6.1) so I could start my configuration.
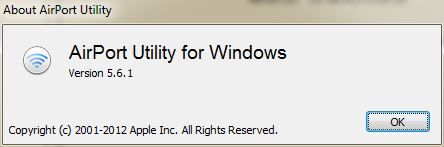
As I looked through the interface I couldn’t find anything related to setting up a guest network. I knew I had seen these configuration options before while configuring an Airport Extreme. Their absence here made me question whether guest network support existed on the Airport Express products.
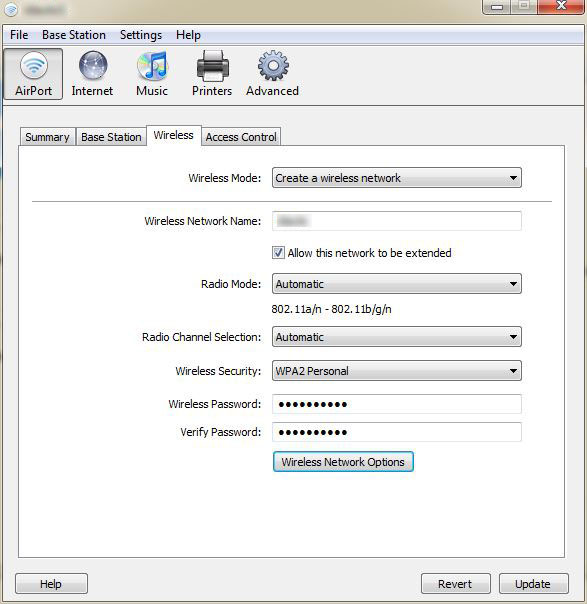
Before giving up I decided to try the Mac version of the Airport Utility. I pulled out my Macbook, ran the utility and Voilà; I could see the guest network settings that I had expected to find. Not a big deal, but it’s helpful to know that the Airport Utility for Windows is lacking in functionality and cannot be used to implement a guest wireless network on an Apple Airport Express.
How It Works
Now that we know how to define our network, we need to figure out how to make the guest network coexist with the rest of our configuration and how we can keep its traffic separate from our internal traffic. Since I have no interest in running an Airport Extreme as my router, I configured my Airport to operate in bridge mode, which means I’m using it as an access point only. I then plugged a patch-cord into the Airport’s WAN port and plugged the other end into my switch.
A quick test revealed that I could now access resources from both of my defined wireless networks. This begs the question, how can we differentiate the guest traffic from the non-guest traffic? Furthermore, how can we limit what guests can access. The answer lies in what Apple does to the packets that come in over the guest network. As you might have already speculated, there’s no magic here, Apple simply tags the packets with a VLAN id, which happens to be hard-coded to 1003.
Explaining how VLANs work is beyond the scope of this post, but suffice it to say that with VLAN tagging, we can manage our traffic more effectively even if that traffic is running across the same wire/network. In our case, that means I can use the same access point to allow employees access to the internal network and the internet while limiting guests to internet access only.
The Router
I love building routers and I regularly vacillate between a pfSense router and, my true love, a Linux based iptables router. In this instance, I’m using pfSense to manage my traffic. All I need to do is create a VLAN interface for our 1003 tag, setup DHCP for the interface, define my outbound firewall rules and I’m done.
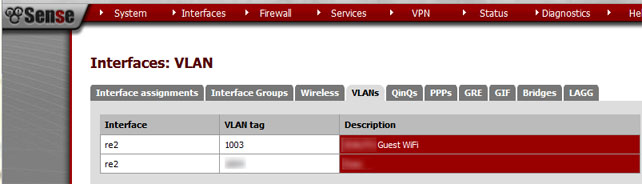
I won’t cover it here, but I also recommend the use of a captive portal for your various networks. I use a portal for my LAN as well as my employee and guest wireless networks. This allows me to effectively throttle bandwidth usage while also limiting which devices have access to my network.
Until next time – GEEK OUT!
~GT~


Great info James
Thx really useful 🙂
I would love to see you cover an article on captive portals. I’m struggling to set it up using pfsense and my apple airport extreme. Thx for the great info